Post-PC Devices: What Is Your Definition?
Greetings. Here at Forrester, we are encouraged to think Deep Thoughts about Matters of Great Importance. Looking across the broader landscape of IT — of which security and risk is just a small part — we can see that one of the biggest and more important matters today is the influx of consumer-grade mobile gear into the workplace. Whether you call it Tech Populism (a favorite Forrester term) or Executive Bling (a favorite term of mine), it is no secret that enterprise CIOs are receiving lots of pressure to support unsanctioned devices like the iPhone and iPad in the workplace.
Today, Forrester published my report “Apple’s iPhone And iPad: Secure Enough For Business?” In it, we describe how the capabilities of Apple’s iOS 4 make these devices secure enough for many businesses to use safely. We define seven security policies every enterprise should implement to keep its email and corporate information safe on Apple mobile devices, whether or not the enterprise owns them. We also define additional security "high-water marks" — policies and processes you can implement — based on your risk profile and regulatory exposure. I hope you’ll read the report, and I welcome your comments and questions.
The iPhone and iPad are two good examples of post-PC devices. These devices have five essential properties. Post-PC devices devices are (a) small, pocketable gadgets that (b) run compact operating systems designed for mobility. Applications that run on these devices are (c) easily installed by customers and (d) execute under a trusted applications runtime. Unlike traditional PCs, post-PC devices are (e) not general-purpose computers that run general-purpose operating systems.
Examples of post-PC devices are the Apple iPhone and iPad, Android mobile phones, BlackBerry, and the Amazon Kindle. Windows Mobile is a mobile device, but not a post-PC device. Windows Phone 7 will likely fit the definition of a post-PC device when it is released in later 2010 or early 2011. As the chart below shows, data from my colleague Sarah Rotman Epps shows that the number of consumer post-PC devices (tablets, eReaders, internet-capable mobile phones) will eclipse PC devices (desktops, laptops, netbooks) sometime this year.
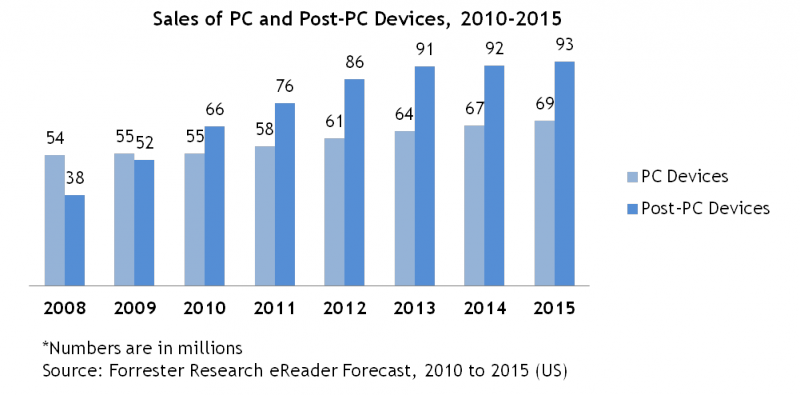
The fascinating thing about post-PC devices is that they have an entirely different, and much stricter, security model than open-ended, general-purpose PC operating systems. The three key characteristics of this model are (a) a trusted boot process, (b) mandatory application signing, and (c) application sandboxing that limits what resources a customer-installed application can access. Because they are much more locked down, malware as we know it today won’t be a problem, although spyware is quite likely. And that, in turn, means that the kinds of security products and services enterprises will need will be different than what they need today.
How and why the security needs of enterprises will change is the subject of my next report, “Security In The Post-PC Era,” which I am currently researching. I would enjoy hearing from Forrester customers about their perspectives on this subject. If you have a large deployment of iPad devices planned, or are enrolling employee-owned Android or Apple mobile phones into your e-mail system, please send me an e-mail. What security risks did you identify? Which ones did you choose to address or ignore? How has employee ownership of these devices changed your perceptions of the issues?