Announcing The Forrester Wave™: Attack Surface Management Solutions, Q3 2024
We’re excited to announce the inaugural release of a Forrester Wave™ evaluation covering attack surface management (ASM) solutions. We evaluated the 11 most significant ASM vendors in what is currently a rapidly evolving market segment. Forrester covers ASM and periphery markets such as exposure management and vulnerability risk management (VRM), as these segments all contribute to proactive security, supporting use cases of visibility, prioritization, and remediation. For the ASM Wave, we primarily focused on how ASM solutions provides the first essential step for proactive security: visibility.
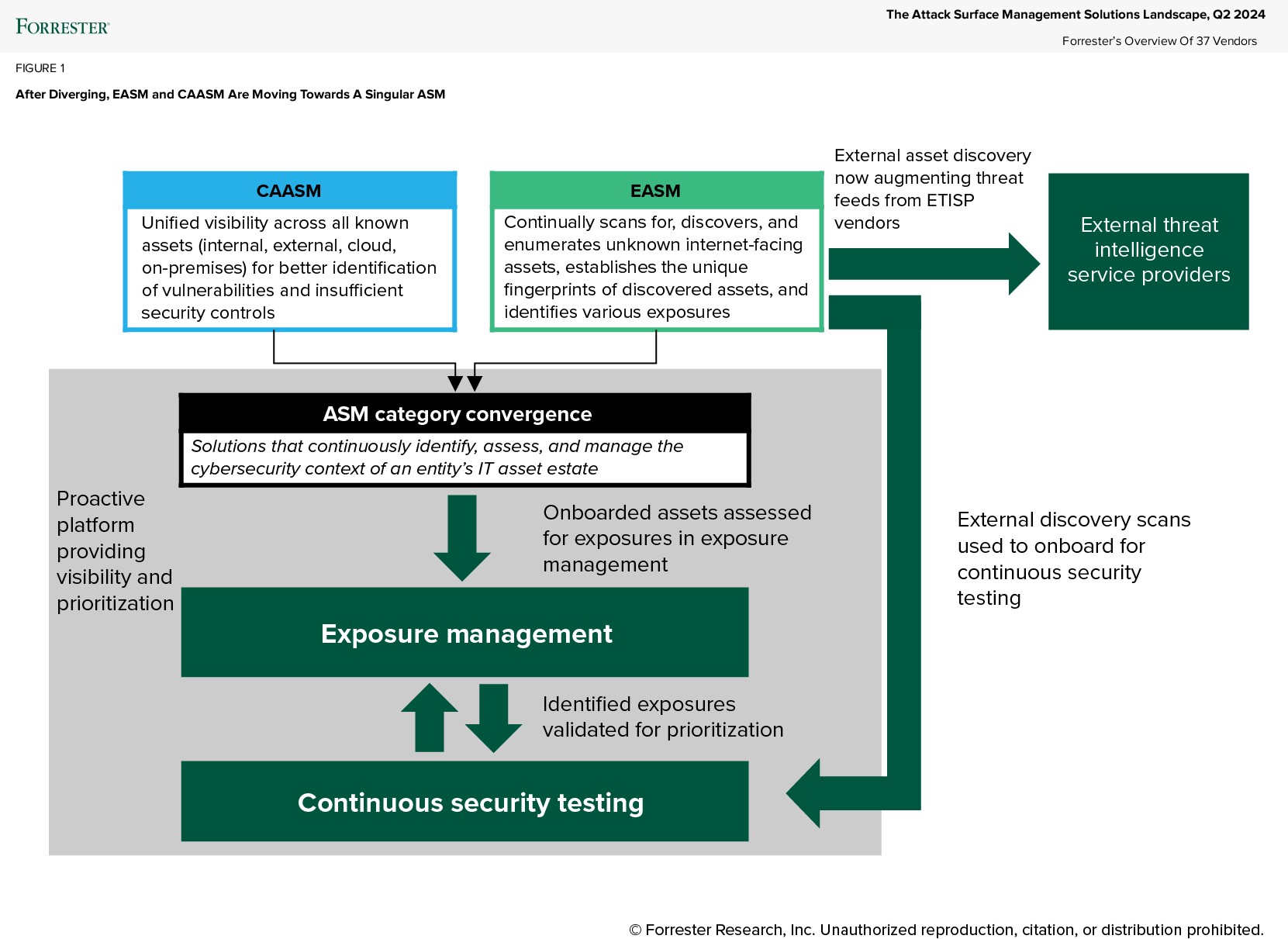
What’s Going On With The Attack Surface Management Market?
For the ASM Wave, we evaluated vendors that started off as cyber asset attack surface management (CAASM), external attack surface management (EASM) solutions, or vendors that package ASM as part of their SecOps platform strategy, including those that deliver ASM capabilities via an exposure management offering. All vendors evaluated are aiming to provide comprehensive visibility into assets and attack surfaces to enable customers to prioritize and ultimately remediate risks. The state of attack surface management is volatile and dynamic (see figure below), which we took under consideration in the Wave evaluation. Some key considerations for today’s state of proactive security include the following:
- CAASM and EASM have merged into a singular ASM to support visibility use cases. CAASM and EASM have always provided visibility, through either an internal (defender) view or external (attacker view). These related use cases provide visibility and are improved when combining both views — which users can obtain now from CAASM, EASM, or ASM integrated within a SecOps platform. As our Wave details, CAASM features can differentiate by extending a breadth of integrations that ingest asset context, and EASMs can differentiate when vendors own and deploy proprietary scanning technology.
- Standalone EASM looks more like a threat intelligence product. EASM has turned into a capability to be found in a variety of products, most notably in threat intelligence providers that are expanding external pictures of environments — not just externally facing assets but also capabilities such as malicious brand impersonations on social media or mobile app stores, executive monitoring, and third-party/supply chain monitoring.
- EASM and continuous security testing augment one another. When assets are externally discoverable and accessible, the next strategic step in proactive security — prioritization — is testing them to assess the vulnerabilities. For this reason, continuous security testing companies that offer breach and attack simulation, bug bounty, or penetration testing-as-a-service capabilities have added EASM capabilities. Proactive security vendors need to support more than just visibility or prioritization to extend a platform offering. Since ASM is focused on visibility and continuous security testing supports prioritization, we expect to see ASM and continuous security testing vendors continue to add to one another’s capabilities.
- Proactive security platform approaches to attack surface management are most prominent. ASM will continue to prevail as a capability in proactive security platforms to provide visibility. Proactive security platforms today extend and will continue to enhance prioritization through features such as exposure management, CISA KEV/EPSS/CVSS or risk scoring (typically found in VRM solutions), or continuous security testing. ASM solutions integrating into a proactive security or SecOps platform with the data that platform already possesses is a crucial differentiator here, because it provides out-of-the-box asset context and stepping stones to exposure management as part of a prioritization strategy.
A Proactive Security Approach Will Future-Proof Vendor Rebranding, Category Shifting, And Your Program Strategy
Until, and if, the proactive security market stabilizes around one category, continue to ask yourself how much visibility you have, whether your prioritization strategy is maintaining acceptable risk thresholds, and how well you remediate vulnerabilities. These will always be the core principles you need to fulfill even as market landscapes change. Today, ASM solutions provide visibility externally and internally. This visibility needs to be accessible for your prioritization strategy (whether through exposure management, VRM-provided risk scores, or continuous security testing) and needs to be the source in and out of your remediation tracking (whether through VRM, ITSM, or SIEM).
Forrester customers who have questions or concerns about ASM and these other complementary markets should schedule an inquiry or guidance session with me to review how you can ensure that your organization is on the right path for effective proactive security.
