Assessment Is Anyone’s Guess: Proving GOAT Status Requires Validation
As spectators tuned in to Super Bowl LIX to indulge in American culture rife with consumerism, T. Swift, and rap feuds, the buzz was less around the game and more on determining who is pro football’s GOAT (greatest of all time). Kansas City Chiefs quarterback Patrick Mahomes had an unprecedented opportunity to win a third consecutive Super Bowl, the fourth in his young career, which raised questions from sports analysts of whether Mahomes was surpassing the legacy of another NFL GOAT, New England Patriots QB Tom Brady. It seemed like sports media had already declared Mahomes as the new GOAT, but first, Mahomes would have to win this year’s Super Bowl versus the Philadelphia Eagles to cement this status.
That didn’t happen. Instead, a tough Eagles defensive front brought constant pressure that disrupted Mahomes, leading to several costly turnovers. The Chiefs could not overcome the Eagles’ preparation and the effectiveness of their defensive schemes, which validated Philadelphia’s defensive preparations.
Validation showed its GOAT-head during the Super Bowl’s commercial breaks, with cybersecurity vendor Pentera’s ad about a half-goat/half-CISO that transformed from being his organization’s scapegoat to the cyber-greatest of all time. Becoming the cyber-GOAT, they say, requires continuous and proactive testing for vulnerabilities. Forrester’s proactive security research outlines visibility, prioritization, and remediation as the core principles of proactive security, with validation being a means to enhance accuracy and focus in prioritization. Vendors such as Pentera, XM Cyber, and Horizon3.ai provide validation that vulnerabilities are exploitable as a means to drive prioritization.
Cyber threat exposure management is used by some vendors to describe this prioritization strategy. This is an unnecessary term in an already crowded world of cyber acronyms. Instead, organizations should focus on how to build proactive security programs with prescriptive, use-case centricity — using the three proactive principles to understand how organizations are gaining visibility, prioritizing exposures, and ultimately remediating them.
Exposure management is a prioritization strategy and can be one of many prioritization strategies that organizations use. It maps exposures on an attack path and assesses the potential that an opponent could breach them — much like how Chiefs and Eagles head coaches Andy Reid and Nick Sirianni built out their Super Bowl game-day plans and playbooks. But you can only validate the effectiveness of offensive and defensive schemes in the game itself. In cybersecurity, this is how penetration testing and red teams provide singular, point-in-time validations. But now organizations are looking to do these continuously. This is where continuous security testing comes in, which we outlined in our recent report, Strengthen Proactive Security With Continuous Security Testing.
Continuous security testing validates and proves that vulnerabilities are exploitable. There are many ways that continuous security testing can factor into remediation prioritization strategies today. Other options include breach and attack simulation, bug bounties, and penetration testing as a service, which all have different use cases and scopes (see image below). And while these are different options that factor into remediation prioritization, it’s likely that your organization will still utilize other prioritization methods such as CISA KEV, CVSS, and EPSS, depending on asset types and circumstances.
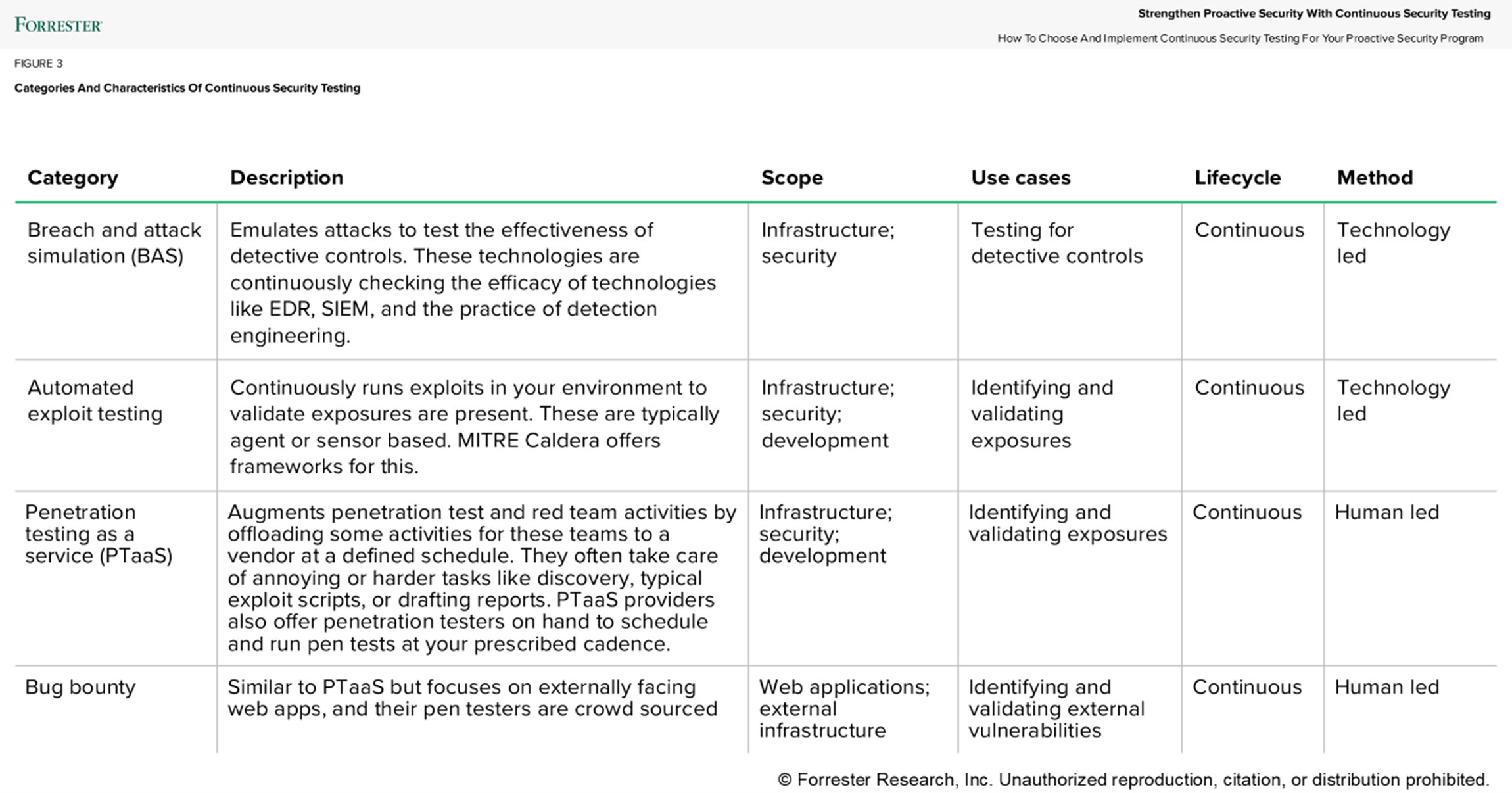
Should you do continuous security testing? Before jumping right in, we recommend that security and risk pros first assess how they are gaining visibility into assets and vulnerabilities — our first principle of proactive security. Next, teams should perform assessments of vulnerabilities with vulnerability scanning and combining their increasingly omnipresent sources of vulnerabilities. From there, teams can form their prioritization strategies. Consider exposure management as one of these and improve it with continuous security testing that validates that exposures are exploitable. But don’t forget remediation plans — this use case is often neglected in proactive platform companies (and why we expect to continue to see consolidation in the proactive security market, as companies such as Tenable acquire Vulcan Cyber to enhance remediation processes).
Let’s talk! If you want to talk more about proactive security or continuous security, book time with me.
