The Top Seven Most Misused Terms In Cybersecurity
A common point of confusion in inquiries, briefings, and advisories is the difference between a vulnerability, a threat, and an attack. Do you detect a vulnerability? Is an exploit an attack? The answer to both these questions is no.
It’s easy to conflate all these terms in the course of overzealous marketing, but ultimately, words matter.
Sufficiently complex domains require a shared vocabulary to communicate depth of meaning. It’s why sailors use the terms “port” and “starboard” instead of “left” and “right.” It’s why we have MITRE ATT&CK for communicating about threat actor techniques.
When different vendors or practitioners use different words to communicate the same thing, we inevitably talk past each other and often end up confused. It’s like the ’90s again, with everyone lobbying standards bodies. But truly, it steepens the learning curve to enter an already complicated field and promote a nonstandard nomenclature between partners — some of whom are just entering the field themselves.
Without a common vocabulary, we also can’t clearly and effectively achieve other necessary outcomes. This blog defines these common security terms with examples of how they’re used so we can (hopefully) stop the madness.
Definitions For Commonly Misused Security Terms
Flaw: A flaw is any unintended functionality in an application. A flaw can become a vulnerability, but not all flaws are vulnerabilities. This term is commonly used in application security.
AKA: weakness
Example of this used correctly: The application had a flaw that allowed users to access customer data.
Example of this used incorrectly: The flaw was intended by the developer.
Vulnerability (noun): A vulnerability is a flaw in an asset such as a device, application, or security program that can be exploited. Resolving vulnerabilities stands out as one of cybersecurity’s longest-running, unsolved — or partially solved — problems. A vulnerability can be exploited in the course of an attack.
Example of this used correctly: The vulnerability was exploited during the attack.
Example of this used incorrectly: The vulnerability was innocuous.
Finding: A finding is the identification of a flaw or vulnerability. Static application security testing (SAST) and dynamic application security testing (DAST) tools identify findings that may or may not be known vulnerabilities.
AKA: flaws/defects/vulnerabilities found
Example of this used correctly: Our SAST tool had five findings.
Example of this used incorrectly: One finding was an exploit.
Exploit: An exploit is a procedure designed to take advantage of a vulnerability. To paraphrase a blog from Veracode, an exploit is the weaponization of a vulnerability for a specific purpose. Exploits may be used in the course of an attack to gain access, escalate privileges, or perform other functions.
Example of this used correctly: An exploit was used during the attack.
Example of this used incorrectly: We analyzed the software and confirmed an exploit was present.
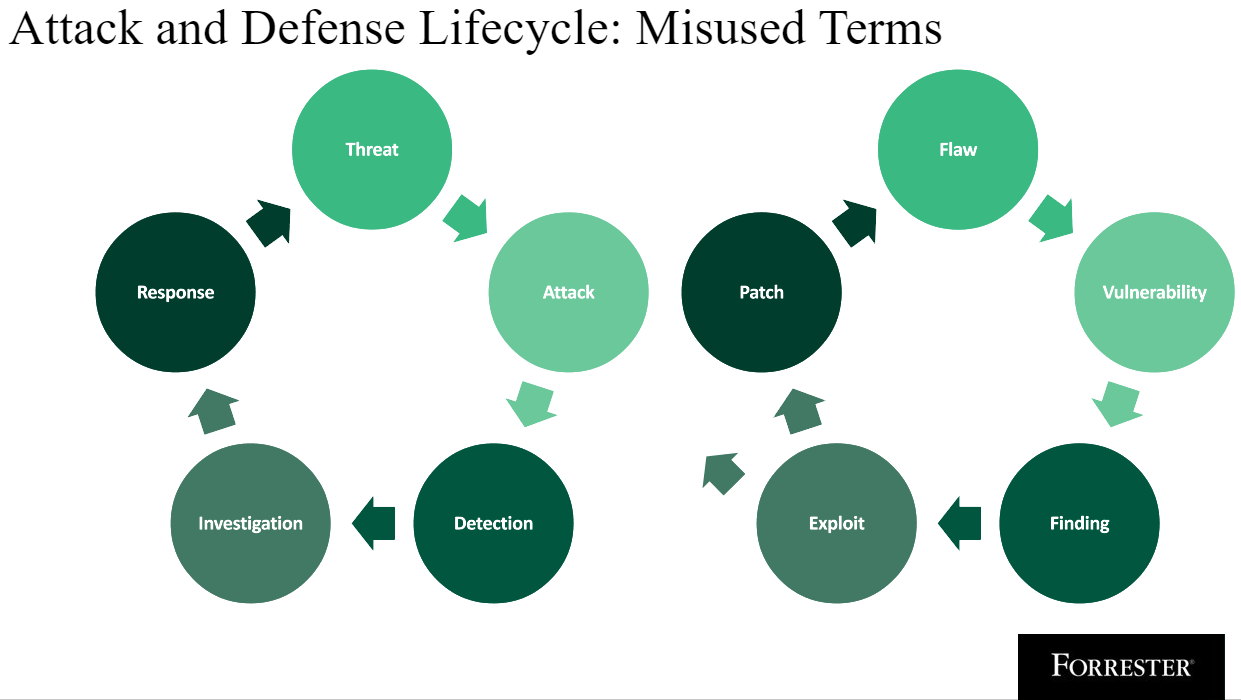
Threat: A threat is a potential attack that has not yet taken place.
Example of this used correctly: Ransomware is a threat to our organization.
Example of this used incorrectly: A finding is a threat.
Attack: An attack is active, malicious activity that is happening or happened previously. An attack may exploit one or more vulnerabilities to reach its end goal.
Entropy gone wild. Tomorrow’s emergency: today.
Example of this used correctly: An exploit was used during the attack.
Example of this used incorrectly: The attack was a vulnerability.
Detection: A detection is the real-time or retroactive identification of an attack within a threshold of certainty. We’ve found that the term detection is commonly mistaken for “finding” when referencing a vulnerability. This important distinction calls out that a detection is the identification of an attack — not a vulnerability.
AKA: alert, finding, incident
Entropy found in real time. Tomorrow’s emergency discovered: just now.
Example of this used correctly: The detection was of an in-progress attack.
Example of this used incorrectly: The detection was a vulnerability.
More To Explain?
This is a cursory examination of some of the commonly misused words in cybersecurity, but there are many, many more. What did we miss? What would you like us to help clarify for you, your team, or your vendor? Let us know on social media or via email.
