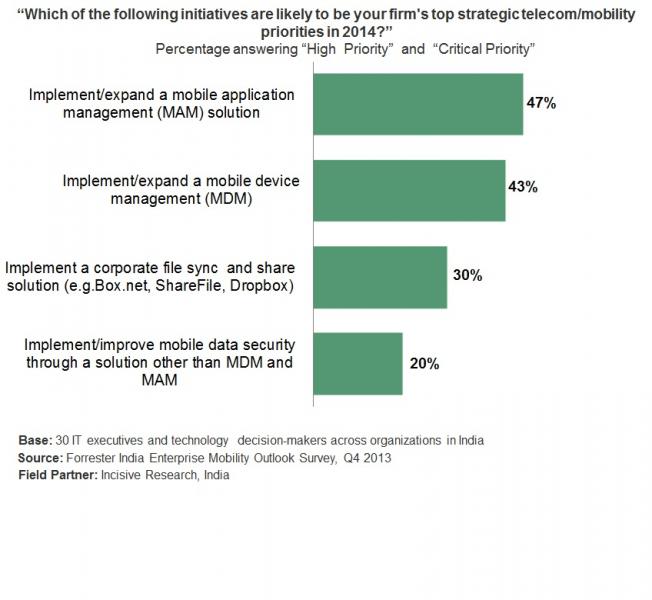
Indian Firms Are Moving Beyond MDM To Focus On Mobile Application Management
Indian firms have become cognizant of the fact that they have entered the age of the customer — an era in which they must systematically understand and serve increasingly powerful customers. These firms are leveraging mobility to empower their employees to win, serve, and retain customers. For example, the Tab Banking initiative by ICICI Bank uses tablets to enable sales representatives to visit customers to give them the convenience of opening bank accounts without leaving their home or office. However, since consumer mobile technologies have entered the enterprise, the management of mobile device platforms has become more complex; enterprises have started realizing that security controls should be around the apps and the data and not the device. In India, mobile application management (MAM) has leapfrogged other strategic telecom and mobility priorities in 2014 (see the figure).
The importance of supporting a workforce that wants (and has come to expect) to work anywhere, anytime, and on any device has necessitated a paradigm shift in security and risk (S&R) mitigation approaches and techniques. S&R professionals must therefore implement a security program that centers on mobile applications. This is because:
- S&R pros have limited control over mobile network, device, and OS security. The mobile security stack consists of four layers: the carrier/network, the device hardware, the operating system (OS), and the application layer. The carrier/network layer belongs to the telecommunications carrier and is generally out of enterprises’ control. Mobile OS suppliers control the interactions between the OS and third-party vendors looking to manage and secure that OS. The security of the device and OS layers will continue to commoditize as mobile OS suppliers fold new security technologies directly into their offerings while simultaneously limiting expansion on the interfaces available to third-party security management offerings. This leaves the application layer accessible, which S&R pros can easily manage.
- The real security risk is in the mobile application layer. Even though the device hardware and OS layers have published vulnerabilities, attackers are not actively targeting them at a level that poses significant risk. The Symantec Internet Security Threat Report 2013 demonstrated that vulnerabilities discovered within an OS do not directly correlate to the number of threats found in the wild targeting that OS — meaning that the application layer is the primary point of risk on a mobile device.
Enterprises should take a multilayered approach to mitigating security risks. Bringing together technologies from the application, network, and OS layers will lessen the risks of bring-your-own-device and mobility support until single-sourced solutions become available. Forrester’s research report “It’s Time To Level Up Your Mobile Application Security Program” provides actionable advice to S&R pros for supporting their mobile security strategy in 2014 and answers key questions, such as how to create and mature a mobile application security program.