New Research: Know Your Adversary
 Mandiant's APT1 report changed the threat intelligence marketing game, and you would be hard pressed to find a cybersecurity company that doesn't have a research/intelligence team that produces threat actor reports. The previous few weeks have seen a significant amount of threat intelligence marketing around threat actor groups. FireEye released "APT28: A Window into Russia’s Cyber Espionage Operations?" The analytics firm Novetta released "Operation SMN: Axiom Threat Actor Group Report."
Mandiant's APT1 report changed the threat intelligence marketing game, and you would be hard pressed to find a cybersecurity company that doesn't have a research/intelligence team that produces threat actor reports. The previous few weeks have seen a significant amount of threat intelligence marketing around threat actor groups. FireEye released "APT28: A Window into Russia’s Cyber Espionage Operations?" The analytics firm Novetta released "Operation SMN: Axiom Threat Actor Group Report." - You might not be ready for adversary intelligence. (See Forrester's Targeted Attack Hierarchy of Needs research.)
- Misattribution can occur.
- Even the intelligence providers and researchers don’t always agree.
- GeoIP doesn’t equal attribution, but S&R pros often assume that it does.
- Attribution can distract you from more important security initiatives.
- Tracking threat actor-naming conventions wastes valuable time.
- Adversaries can use false flags to throw you off their trail.
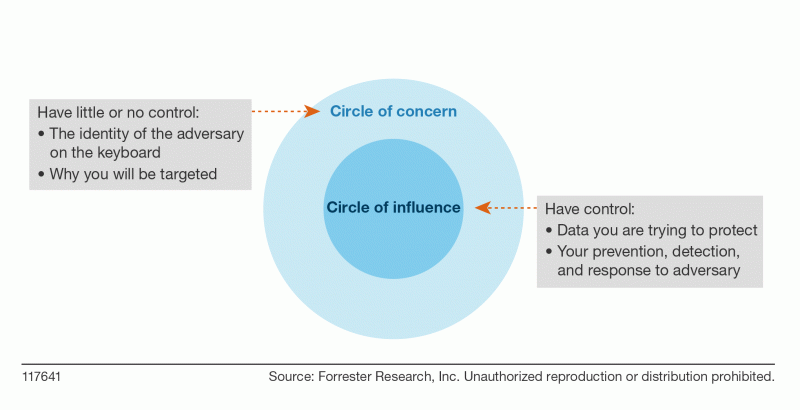
In the research, I include five recommendations to successfully incorporate adversary intelligence into your threat intelligence program. If you are a fan of Stephen Covey’s Seven Habits of Highly Effective People, you will recognize my first recommendation: Understand Your Circles Of Influence and Concern. Proactive organizations focus their efforts on the circle of influence: things they can do something about. Reactive organizations focus on the circle of concern: things they have little or no control over. Adversaries fall more into your circle concern than your circle of influence. I have many clients that hyper focus on the adversary. If you are focusing too much on your circle of concern, remember the following:
- You aren’t a government or law enforcement agency. You don’t have the ability to issue subpoenas and search warrants. While it would undoubtedly be satisfying, identifying who is on the keyboard targeting your organization is a level of attribution that is beyond the private sector. Leave individual attribution to three-letter agencies, and don’t be distracted by something that is clearly in the circle of concern.
- You can take a data-centric approach. You might not always have direct influence over the data you’re trying to protect, but you certainly have more control over it than how an adversary is going to target you. Be proactive and understand what makes your business successful. Use Forrester’s Data Security And Control Framework to: 1) define your data; 2) dissect and analyze your data; and 3) defend and protect your data.
Check out the full report for all the details. If you are a Forrester client, I will be doing a webinar on this research on Tuesday, November 11 from 11 a.m. to 2 p.m. Eastern time. You can sign up here.
Also it is worth mentioning that even if you aren't a Forrester client, I am happy to provide you complimentary research in exchange for a confidential research interview. Direct messages via Twitter are a good way to contact me. @rickhholland