Announcing Analyst Experience: SOC Analysts Finally Escape The Shackles Of Bad UX
Everything in detection and response starts with the security operations center (SOC). It serves as the launching point for many cybersecurity careers, with the security analyst serving as an expert in beginner’s clothing. Organizations depend on security analysts to recognize, classify, investigate, and respond to threats. Per our 2021 State Of Enterprise Breaches report, 63% of organizations surveyed were breached in the past 12 months, and it takes a median of 37 days and a mean of $2.4 million to recover from a breach. The numbers prove that the SOC matters.
But security analysts find themselves equipped with woefully inadequate tools, considering the criticality of the tasks they perform. When SOC analysts sit down in the (swivel) chair for the 8- to 12-hour shift, before they ever see adversary activity, their battle begins … against the technology and processes they have to use. This includes siloed data, horrid integrations, user interfaces that are poorly stitched together from multiple acquisitions masquerading as platforms, and “expert systems” that are both hard to use and hard to master.
That backdrop helped us identify a new — and necessary — trend of security products and services that focus on improving the SOC overall and security analyst workflow: analyst experience (AX).
Forrester defines the analyst experience as:
Security analysts’ perception of their interactions with a particular security product, service, and process across various workstreams.
AX builds on the long history of user experience (UX), customer experience (CX), and employee experience (EX). The rise of developer experience (DX) provides a frame of reference for practitioner-oriented experience frameworks, serving as a blueprint for AX.
AX dares to challenge the status quo with the following question: What if the landing page in portals mattered for something other than as the starting point for vendor sales engineers during demonstrations? Five elements make up AX: discover, explore, classify, determine, and execute.
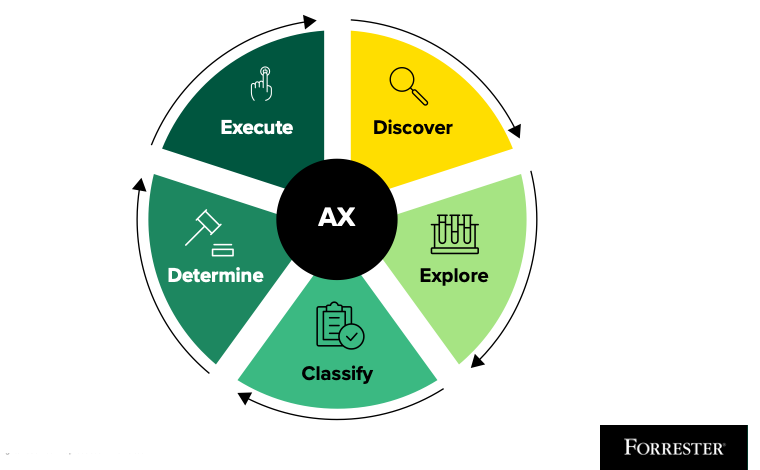
CX pros create journey maps to understand “customers’ lived realities.” AX is the application of journey mapping exercises for security analysts to understand their lived realities. Each element applies to the security analyst’s journey when working an event. This workflow exists for, but is not limited to, the two primary functions of security analysts: detection and response. These functions include examining alerts, investigating incidents, confirming severity, threat hunting, and initiating response actions.
AX will feature prominently in the SOC tech stack: Endpoint detection and response (EDR) and security orchestration, automation, and response (SOAR) are areas where convergence began. The emergence of extended detection and response (XDR) and managed detection and response (MDR) foreshadow the impact of AX. And given the fact that every product eventually becomes a service, as we mentioned in our “Security Services Flywheel” blog, expect to see AX there as well.
Our upcoming threat hunting research will demonstrate how to incorporate AX into additional detection and response tasks.
For more on AX, check out the full report: Analyst Experience (AX): Security Analysts Finally Escape The Shackles Of Bad UX.
