Threat Hunting 101: A Human-Led Exercise
Threat hunting is a term frequently misused by cybersecurity pros, vendors, and service providers. We researched threat hunting to determine what it really is and what benefits it brings and to overcome the misuse and abuse of the term. The resulting report, Threat Hunting 101, published recently.
We’ve heard threat hunting described as “automating analytics,” “investigating an alert,” or even “running searches for indicators or artifacts in an environment.”
Threat hunting is none of those things, but it may include or become any of those things. It might use them as inspiration for a hypothesis or tactics during a hunt, or it become one of these if the threat is high fidelity. But at best, those are inputs or outputs in a threat hunting program. Forrester defines threat hunting as:
A practitioner-led, hypothesis-driven exercise to find attacks that circumvent detection capabilities in cybersecurity products and services.
Threat detection finds needles in the haystack. Threat hunting exists to find the sharpest, hardest-to-find of those needles. No security tool can detect every attack. Cybersecurity pits adversaries against defenders. Defensive technologies rely on rules, heuristics, and outliers to find evil. Those technologies lack one essential component that threat hunting introduces: harnessing the creativity of practitioners defending enterprise environments.
Sharpen The Skills Of Your Team … And Open New Career Paths For Talented SOC Analysts
We discuss several benefits in our full report, but we’ve included a specialized set in this blog. These benefits focus on the skills of the practitioners on your team. Combine them with what’s in the full report for a more exhaustive list. A few reasons it’s in the best interest of your team to start threat hunting:
-
- Create new career paths for security operations center (SOC) analysts. Threat hunting is a career path that doesn’t require analysts to go the traditional manager route or leave the SOC entirely. Let SOC analysts gain repetitions in seeing adversary activity in real time as an analyst and eventually apply that body of knowledge to seek out adversary activity as a threat hunter with extensive experience in the environment.
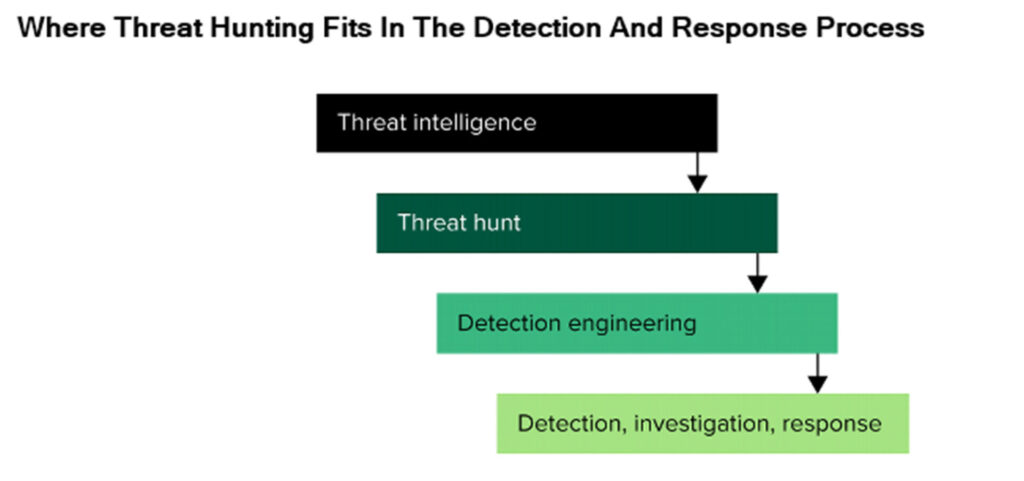
Forrester clients, check out the Security Analyst and Threat Hunter role profiles for more information on these important roles in the SOC. - Help your team hone detections. Threat hunting has an important output: new detections, which result in continuous improvement in security operations. It enables security teams to turn missed attacker behavior into new detections by reflecting on how adversary tools, tactics, and procedures bypassed existing controls. Threat hunting fits between curated threat intelligence and detection engineering in your detection and response processes.
- Use it as an assurance exercise. A new piece of research on the latest ransomware variant drops, and you and your team have no idea if you’re a target. What do you do next? Launch a hunt and look for known TTPs based on research without waiting for a vendor to update its signatures. Threat hunters can formulate a hypothesis around a particular piece of malware, campaign, or threat group and determine whether it is present in the environment.
- Create new career paths for security operations center (SOC) analysts. Threat hunting is a career path that doesn’t require analysts to go the traditional manager route or leave the SOC entirely. Let SOC analysts gain repetitions in seeing adversary activity in real time as an analyst and eventually apply that body of knowledge to seek out adversary activity as a threat hunter with extensive experience in the environment.
Threat hunting levels up security operations and plays a critical role in building resiliency for cybersecurity. The program, function, and role validate your existing controls, enhance your detection engineering capabilities, and confirm the effectiveness of your security operations team.
Forrester clients can read more about how to build a threat hunting program in the full report. You can also request an inquiry or guidance session with Allie or me to discuss building your own threat hunting program.
