Announcing The Forrester Wave™: Managed Detection And Response Services, Q1 2025!
The third installment of The Forrester Wave™: Managed Detection And Response Services is now live, and there’s so much to love about the managed detection and response (MDR) services market: fantastic providers, engaged clients, and meaningful outcomes. This year is no different. Forrester clients can access the full report here.
As we mentioned in Choose Your Own MDR Adventure Amid Ever-Expanding Services, the MDR market continues to evolve. New services have launched, vendors have consolidated, and some providers have taken a few steps backward as legacy managed security services provider-style services enter the MDR space to cloud an already fragmented market.
Two of the biggest trends hitting MDR today are detection engineering and security posture management. Detection as code is all the rage for providers and rightfully so. Put simply, the only way to scale detection meaningfully as an MDR provider is to adopt detection-as-code methodologies.
While MDR was born as a reactive service, it needs to become more proactive by assisting clients in making choices that improve their security posture. Providers are taking a key step forward in 2025 through a combination of exposure management, attack surface management, and system prioritization that helps teams improve their overall security posture.
Stats About The Evaluative Research Process
This blog is more than just a research announcement. I also want to share some statistics about what goes on behind the scenes during the evaluation process. And it is a process, not only within Forrester but also across the providers that participate.
Throughout the Wave evaluation process, we:
- Read 290,000 characters of text or approximately 40,000+ words (many, many times).
- Attended approximately 13.5 hours of demonstration briefings.
- Interviewed customer references over 13.5 hours of calls.
- Reviewed over 400 slides.
- Examined 46 case studies.
- Assessed quotes for 10,000 endpoints ranging in price from $400K to $1,000,000+.
Demonstration Scenarios
As part of the evaluation, we asked providers to cover four scenarios during the demonstration portion. These also make excellent potential proof-of-concept cases. The four scenarios that participating vendors demonstrated during the evaluation are mapped to recent incidents happening around the time our research kicked off. The four scenarios are:
Scenario 1: Insider Threat
A threat actor poses as a newly hired employee and gains access. The employee passes through several rounds of interviews and background checks. Upon receipt of their corporate laptop, their user activity includes suspicious/anomalous login activity, system actions, and attempts at file transfers.
Scenario 2: Account Takeover In SaaS Platform
A threat actor gains access to an enterprise software-as-a-service (SaaS) platform via a valid user account and performs actions to gain access to and exfiltrate sensitive corporate data.
Scenario 3: Social-Engineering Help Desk Teams To Gain Access
A threat actor uses various social engineering techniques to obtain credentials and gain access, using existing or installing new remote access tools to persist with the goals of exfiltrating data and extorting funds from the compromised company.
Scenario 4: Software Supply Chain Poisoning
A threat actor takes over a commonly used third-party library that an enterprise uses in an application it sells and hosts via SaaS platforms for its customers. The third-party library is compromised and allows the adversary to access the client’s on-premises continuous integration and continuous delivery platform, as well as access to the source code for the application.
Customize The Wave Based On What You Care About
Forrester clients can browse to this site when logged in and select “Help me find a vendor” and then select what they care about most in an MDR provider. The site will return a ranked list that aligns to their selected priorities. Forrester’s transparency policy — we detail the full criteria, scale explanations, and scores — allows us to offer an interactive experience to help inform the choices our clients make about their providers.
Unfortunately, I can’t show you the results, so there’s some blurring in the image that’s intentional. But as an example, let’s say that you care most about which providers are strongest at a few specific parts of MDR. Here, it’s core MDR capabilities: detection, investigation, and response. Here’s a screenshot of exactly those items prioritized:
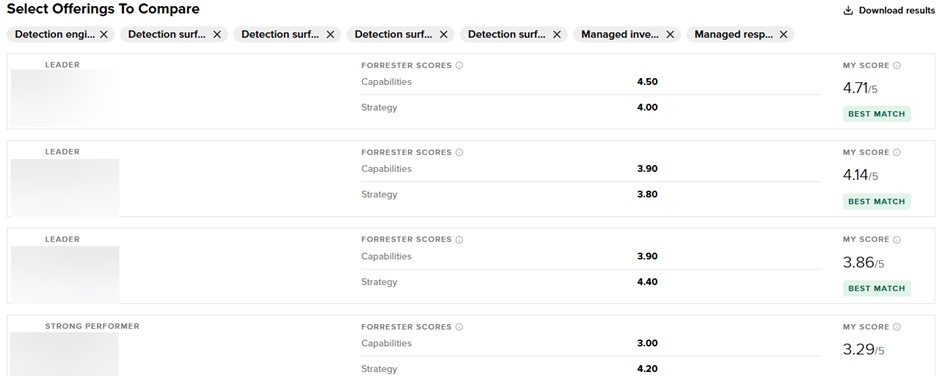
Maybe you are more interested in the providers that can help you improve your metrics, security posture, and vulnerability management processes the most:

You can customize these as much as necessary to narrow down the right vendor for your circumstances.
Forrester clients can read the full report, The Forrester Wave™: Managed Detection And Response Services, Q1 2025. If you have any additional questions, request an inquiry or guidance session with me.
