Black Or Blue, Microsoft’s Quick Machine Recovery Might Be Able To Soften That Bruise
Windows 10 is retiring this year, and we’ve already discussed how business leaders should be moving off that platform to meet compliance goals and reduce the risks of running an unsupported OS. We previously talked about how, until recently, there didn’t seem to be compelling reasons to move to Windows 11. The push to upgrade was simply to maintain compliance and support, which would explain the delays from many IT and security leaders in completing the migration. But within the last year, Microsoft has introduced new features that are only available in Windows 11 that show value for IT and security operations, the latest being tied to the Windows Resiliency initiative.
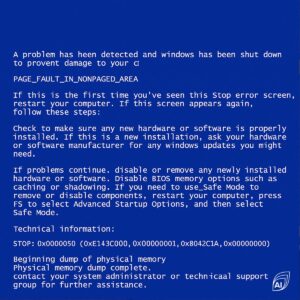
The “blue screen of death” (BSOD) arrived with Windows NT 3.1 in 1993 and since then, anyone who’s spent any amount of time in Microsoft Windows has likely been blessed with its appearance. Every OS has crash handling functions, be it Novell NetWare’s abend or Linux’s kernel panic, but the BSOD is iconic. It’s taken on many faces over the years, but we all know what it means.
The information provided in the BSOD could be valuable to the skilled IT support analyst and methods like the “last known good configuration” boot option offered some relief. But in many cases, the BSOD lacked the depth needed to restore the OS to clean operations.
The latest set of planned changes for Windows 11 include the theme “BSOD is dead, long live BSOD” — as we say goodbye to a blue screen and welcome a black screen. Of course, this just feels more ominous, as a black screen is creepy and the latest color choice for the blue screen was rather soothing. But feelings aside, there will also be options as part of the Windows Recovery Environment called “quick machine recovery,” which will allow IT admins to deploy remediation functions across the enterprise in the event of widespread issues. Some functions will also come to the Home editions, which will be helpful to businesses that allow BYOD to provide guidance to employees on how to get back to normal after something goes wrong.
Following along with these changes is a “nudge” to remove endpoint security operations from the kernel space while still allowing the endpoint protection vendors the ability to monitor and defend the core functions of the operating system. Microsoft has previously said it doesn’t intend to lock approved security vendors out of kernel operations, but many of the vendors in the endpoint security space like what Microsoft is doing to balance kernel access needs with reducing the impact of faults that lead to the dreaded BSOD. This move will not guarantee that kernel faults won’t happen, as no software is perfect and every OS has its failure mode, but each step that reduces the likelihood is a step in the right direction.
Like we said in our report from this past May, Say Goodbye To Windows 10 To Reduce Your Cyber Risk, if your organization is staying with Windows as your default desktop operating system, you need to move to Windows 11. Staying on Windows 10 only increases your risk of compromise and as much as you may have liked the OS, it’s time to let it go. We said back in 2022 that Windows 11 was going to get new functions that showed value and while it may have taken a while for these functions to materialize, it’s better to be positive and embrace the changes that can improve the user experience and the security posture at the same time.