Make No Mistake — Software Is a Supply Chain, And It’s Under Attack
Software is no longer just code written by a team of enterprise developers — it’s a complex, interconnected supply chain. And like any supply chain, the weakest link makes the entire chain vulnerable. From open-source dependencies to build tools, container images, and AI models, every component and every handoff in the process introduces downside risk. Yet most organizations still treat software security as a final checkpoint rather than a continuous, strategic imperative that starts at software selection and runs through software decommissioning. It’s time to change that.
Five Takeaways For Security Leaders
The path to securing the software supply chain will not be easy. To get going, consider that:
- Software is a supply chain, so treat it like one. Just as manufacturers map and secure their physical supply chains, software leaders must do the same. IT asset management and software asset management systems are good places to start understanding your software landscape. Visibility into every component — from direct dependencies to fourth-tier libraries — is essential. Without it, you’re flying blind.
- Open source continues to be powerful but even more risky. With 97% of applications using open source (according to Black Duck’s 2025 Open Source Security and Risk Analysis report) and 70% of critical vulnerabilities stemming from third-party code (according to Veracode’s 2025 State of Software Security report), dependency management is nonnegotiable. And it’s not just vulnerabilities that creep in but malicious packages, where attackers find ways to trick developers and automated build systems to download legitimate-looking libraries embedded with malicious code using techniques such as typosquatting, dependency confusion, and slopsquatting. Malicious packages are on the rise — up 156% year over year (according to Sonatype’s 2024 State of the Software Supply Chain report). Know what’s in your code.
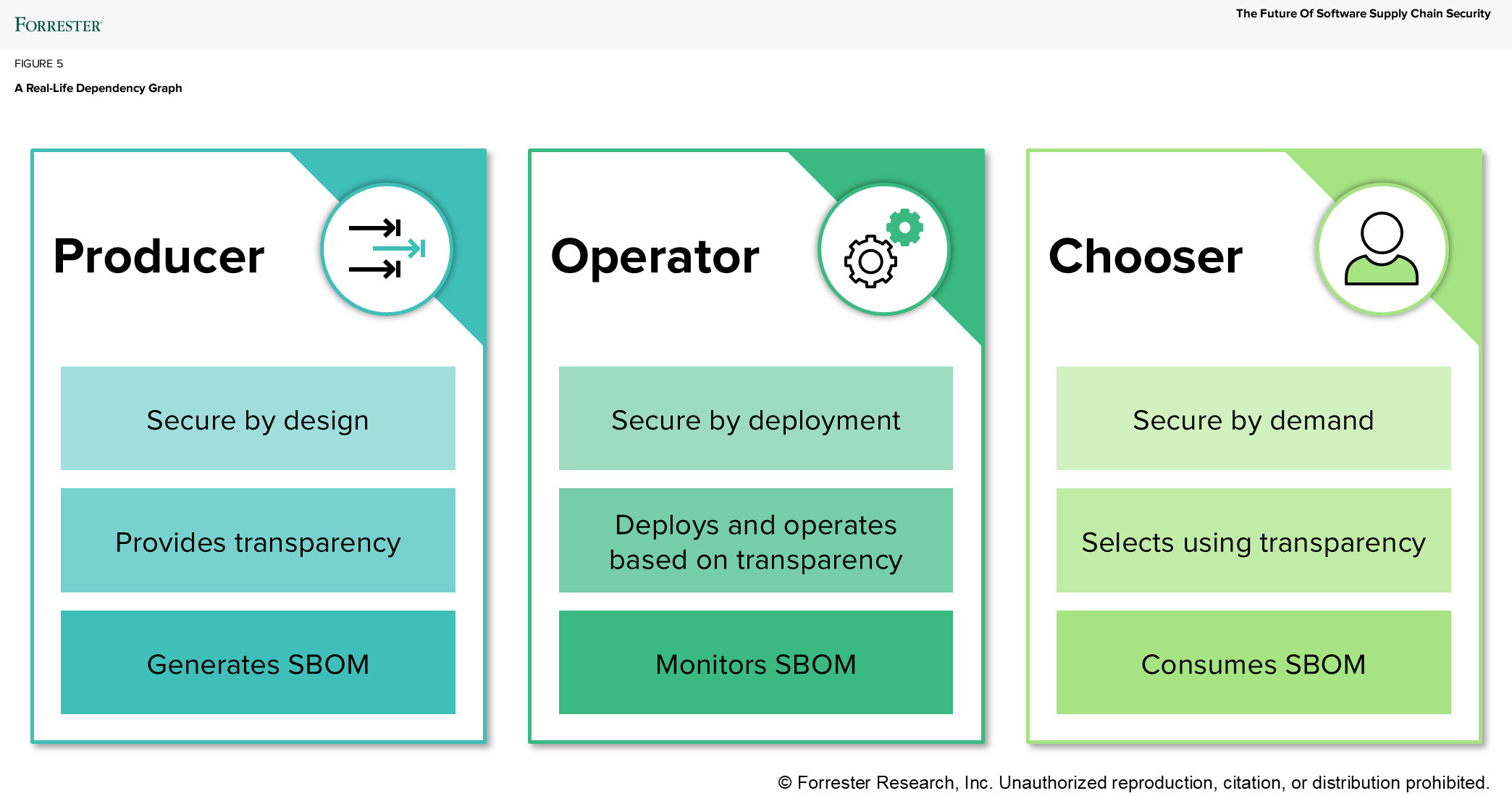
- Know your role and whether you need to secure by design, by deployment, and/or by demand. Your role defines your responsibility (see the figure below). Producers must build secure software from the start. Operators must deploy and maintain it securely. Choosers must demand proof-of-security best practices before purchase. Most organizations play all three roles — and must act accordingly.
- SBOMs are no longer just nice to have. A software bill of materials (SBOM) isn’t just a compliance checkbox — it’s a strategic asset. Producers must generate them, operators must monitor them, and choosers must demand them. SBOMs enable transparency, vulnerability tracking, license obligation visibility, a window into operational risk, and faster incident response.
- There’s no silver bullet, but there is a winning strategy. No single tool, process, or team can secure your software supply chain. Instead, take a proactive approach to safeguarding software throughout its acquisition, usage, development, maintenance, operation, and offboarding to prevent security flaws and attacks. You must involve a cross-section of stakeholders from procurement to risk management, information security to legal, and IT to software development. Securing the software supply chain is a team sport!
Software supply chain breaches are costly. They erode customer trust, damage the brand, trigger lawsuits, result in lost revenue, and lead to higher insurance premiums. But they’re also preventable. Start by defining your role, demanding transparency, and embedding security at every stage of the lifecycle.
Want to dive deeper into securing your software supply chain? Read The Future Of Software Supply Chain Security and schedule a guidance session or inquiry with me.
