Amazon and AWS Moves Further Validate The Value Of Portable Identity
Social sign-in has become a powerful force for marketers and consumers, validating the notion of federated identity in consumer-facing contexts. (Ironic that consumerization of IT is successfully tackling even the single sign-on problem that has bedeviled IT, showing how identity for the top line of the business can overcome resistance in ways that business-to-employee scenarios typically can't.)
But not all consumer-facing federated SSO is social. When I was with PayPal, our team worked on the underpinnings of what eventually turned into Log In with PayPal, which is strictly about federated identity flows for commercial purposes. And today Amazon has come out with Login with Amazon, a powerful statement of Amazon-as-identity-provider. They've been testing this with their own web properties Zappos and Woot; now they're enabling third-party merchants and other sites to use Amazon for authentication of people who already have active Amazon accounts, along with learning a few selected user attributes: name, email, and optionally the zip code of the default shipping addresses. No huge social graphs here, just data that partner eCommerce sites need to function (and make money).
As I discussed in my Outsourcing Identity Assurance research a while back, consumer-facing federated identity puts the focus on volume and the business upside therein, not (formal) verification. Active Amazon customers, numbering 200 million, are already online purchasers. That's super-valuable to merchants considering the relying party proposition, even though it's entirely outside the various government efforts to support "trusted identities in cyberspace" for more and safer eCommerce.
Where is all this going?
- Consumer bring-your-own-identity is going to tie ever more closely to online wallets. PayPal's offering is mature enough to include a seamless checkout option for merchants; Amazon will eventually need to go here as well. 1-Click for third-party purchases tied to Amazon login and backed by AWS-fueled fraud management, anyone?
- Federated login is going to become as common as local account login for social, commercial, and citizen-facing use cases. In some cases, this will mean "NASCAR" login interfaces with a sea of IdP logos; in others, such as with Amazon and Zappos today, you the customer will get a single choice, like it or lump it. In the former case, we're going to see "Forgot your IdP?" as often as "Forgot your password?" (On this topic, stay tuned for new research we've got coming out on customer-facing authentication, which discusses the usability/security challenge.)
Separately, Amazon Web Services came out with interesting identity news of its own, unveiling something called Web Identity Federation as their answer to the challenge of propagating end user identities into developer/application/API contexts. There's now a lot of identity and credential data being flung around in cloud and mobile situations; let's try and tease them out. In my recent report API Management For Security Pros, I presented this diagram:
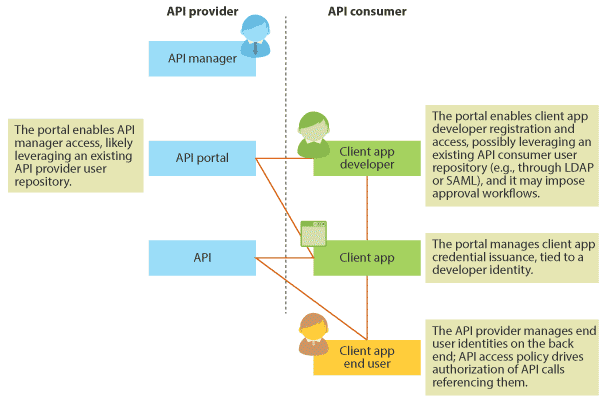
AWS already knows about developer and app identities (the entities in green), but the actual end user of the app (the entity in orange) may not be known yet. In fact, that person may not even have an Amazon login, much less AWS credentials. So Web Identity Federation is its bid to enable inward propagation of the end user's chosen identity (which could be hosted by Amazon or even Facebook or Google – yes, AWS is becoming an equal-opportunity relying party) for proper access control, personalization, and so on. A new Security Token Service (STS) API helps manage all the cross-domain "flinging." It's good stuff, and about time; this was becoming a competitive catchup issue. Microsoft's Windows Azure already has a fairly well thought-out answer to this problem.
What to take away from this news, then?
- Zero Trust run-time identity propagation will be the name of the game for all cloud and mobile services. We can no longer tolerate IAM silos for different purposes and populations; there's no such thing as a B2C or B2E identity in isolation anymore, and now we have to account for B2D (business-to-developer) identity too.
- Emerging standards have set the bar for cloud platform security and identity. These standards, heavily leveraging OAuth and JSON Web Tokens, are the lowest-cost way to do serious, agile, mobile-friendly security and identity. Don't stand for any less.