Six Aspects To Palo Alto’s Acquisition Of CloudGenix
On March 31, Palo Alto Networks announced the intent to acquire CloudGenix, a software-defined WAN appliance vendor. This was another announcement in a long list from the security and networking industries about merging together SDWAN and security. Such combinations are inevitable because:
- SDWAN adoption hasn’t matched the hype. Here is a dirty little secret: SDWAN adoption wasn’t doing that well. Yes, there was a ton of hype about SDWAN adoption, but it was just that: hype. Don’t get us wrong. Forrester’s “SDWAN — More Than Just Cutting WAN Costs” report highlights many valid reasons why companies have been looking to adopt SDWAN capabilities. Over the last 12 months, SDWAN companies have been gobbled up or quietly disappeared. The telcos have shown minimal bumps in SDWAN revenue. Multiple pieces are missing for SDWAN to enjoy a higher level of adoption.
- Lack of security is the major hurdle. Many infrastructure and operations (I&O) teams that indicated their organizations were going to adopt SDWAN ran into a roadblock: security. SDWAN made it much easier to create WAN fabrics to support a hybrid infrastructure, but WAN fabrics expose multiple attack vectors that were once limited to a single location with the traditional WAN hub-spoke architecture. This is one reason why the market has been so excited about security vendors or SDWAN vendors incorporating capabilities or vendors from each other’s side, such as Fortinet rolling out an SDWAN upgrade to the FortiGates.
- Market growth is at the edge. The reason for excitement over SDWAN and security merging comes from the security side of the market. Data centers have been profitable areas, but that is only a drop in the bucket of where money will be spent when you compare new investments that will be associated with internet-of-things (IoT) adoption. IoT will be net-new networking, compute, and storage equipment to support all the new IoT devices, data, and applications. Data-center-centric companies — such as hypervisor, security, hardware, and other technologies — have been doubling down on marketing efforts to create more of an edge presence. And why not? With about 50 billion new devices that didn’t exist in the technology realm, this means new revenue streams associated with all the new applications, data, and services. Would vendors rather sell a dozen items to McDonald’s data centers or over 30,000 to its quick service restaurants?
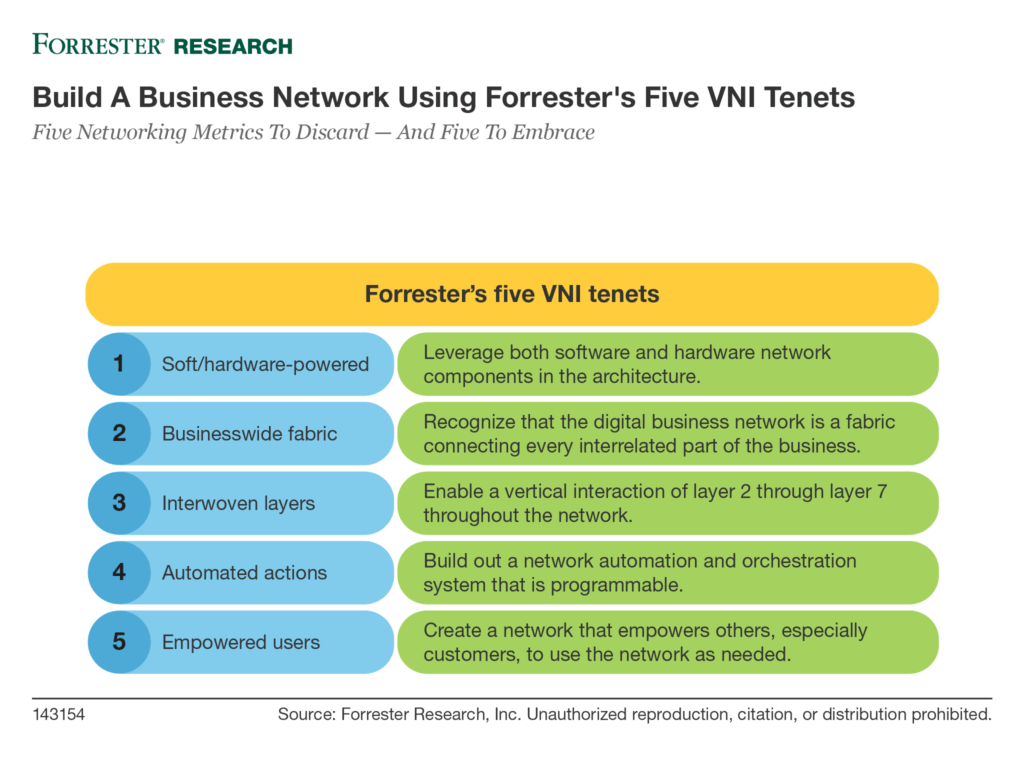
I&O professionals shouldn’t feel like this means that they need to procure and deploy solutions that have security and SDWAN capabilities built within the same piece of hardware from the same vendor; however, the need for security is real. Forrester’s “Five Tenets Define Virtual Network Infrastructure, A Bold New Business Network” report explains in tenets 2 and 3 that services historically deployed within data centers will be spread out to all parts of the business (see the figure below). This is because of IoT, dispersion of data from private data centers to cloud and edge, applications morphing into microservices across business resources, and the adoption of Zero Trust practices. With that in mind, note that:
- This has been done before. We have been down this path a few times over the last decade. Networking vendors tried to lock customers in by trying to create remote office in a box (ROBO) — combining routing, switching, wireless, firewalls, voice over IP, and/or Wi-Fi access points in a single appliance. Due to the radically different needs of manufacturing sites vs. fast-food restaurants, for example, these solutions haven’t done well. Undoubtedly, the security and SDWAN needs of a Best Buy compared to a Marriott will be very different. A single vendor will struggle to meet the needs of multiple verticals. Focus on a system that chains together multiple services as needed rather than relying on a single hardware platform. Microsoft, Google, and Facebook do this at the edge of their WANs.
- The current concept isn’t the end-all and be-all. First, increasing trust levels is more than just adding firewalls to a networking appliance. Second, the security industry will evolve and products will mutate or new ones will rise up as WAN limitations make many vendors rethink their designs. This means some cloud-based functionality will move to the edge — like edge compute. Security functionality will evolve; Forrester’s “A Practical Guide To A Zero Trust Implementation” report highlights the redrawing of lines and shifts in security services. Beyond security services, consider that these locations need to still leverage optimization technologies or global load-balancing information. This is why building infrastructure that can service chain virtual and physical services from multiple solutions will be so critical to the success of supporting a businesswide networking fabric.
- This is a step in virtualizing the network journey. Much as we saw missteps in the data center (DC), the industry is repeating the same mistakes outside of the DC. The industry got irrationally exuberant about manipulating switches and hyper-focusing on the technology method, such as OpenFlow. The real goal is a holistic networking approach that looks at all the data center components, including the business needs. The entire network needs to have the ability to program, automate, and orchestrate the networking services to serve the business and its goals in mind. This is tenet 5 of virtual network infrastructure. Intent is the new buzzword. The software-driven WAN needs to be built around intent, too. Security and SDWAN are just components. You should focus on building an infrastructure that reacts to business needs.