Are You Making These DevSecOps Mistakes? The Four Phases You Need To Know Before Your Code Becomes Your Vulnerability
In Forrester’s Security Survey, 2024, 56% of security decision-makers at firms that experienced an external attack indicated that the breach was the result of an application-related exploit. Why do we continue to be so bad at this!? Part of the problem is that the journey to DevSecOps is bumpy and long. But don’t give up! We’ve identified four key phases of the DevSecOps journey (prepare, crawl, walk, and run) as well as the best practices in each phase to either jump-start your transformation or restart your journey. Some brief highlights from our research:
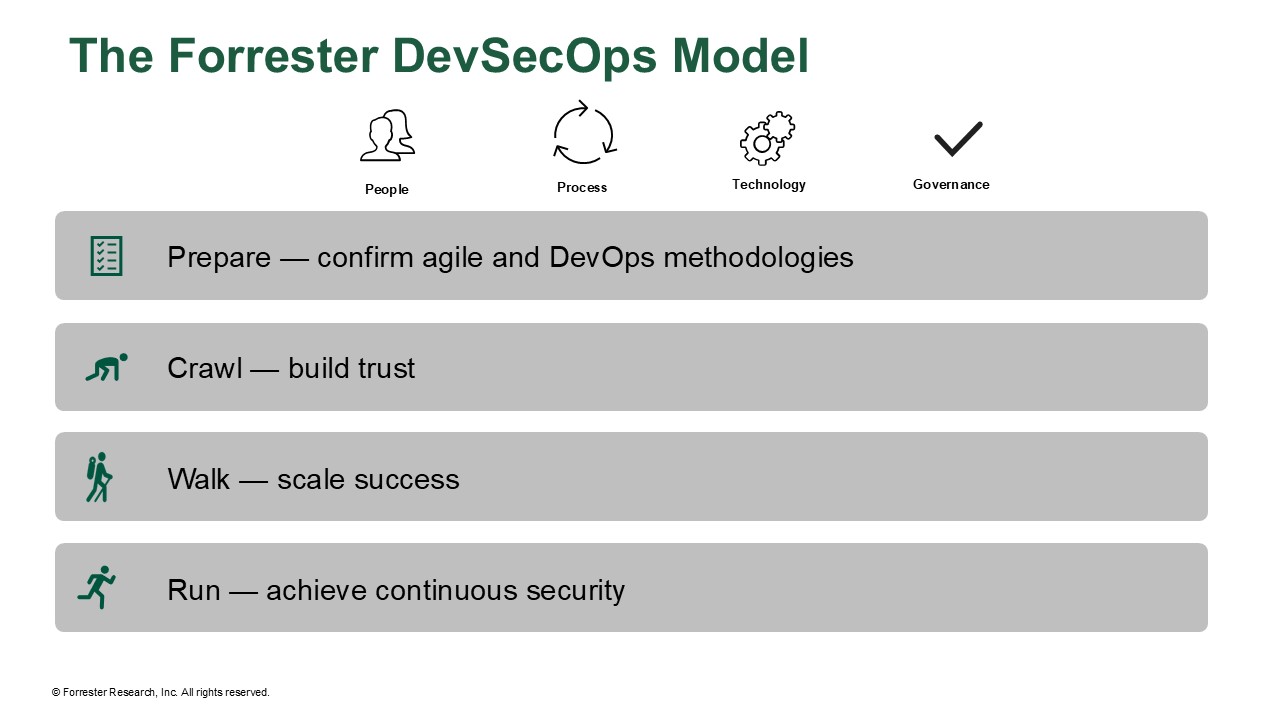
- Prepare for your DevSecOps journey by first confirming your agile and DevOps methodologies. Organize DevSecOps practices around cross-functional product teams. This team will work within agile sprints to continuously integrate, test, and deliver code to ensure quality and reliability, even with frequent deployments. These teams will use key performance indicators to measure the effectiveness and efficiency of DevOps practices. Teams will often use the DevOps Research and Assessment (DORA) 2024 performance indicators as a guide. Monitor these metrics carefully as you progress to course-correct when DevSecOps practices are introduced, but also use these metrics as a basis for DevSecOps ones in future steps.
- Crawl and build trust. Central to this phase is fostering a culture of collaboration and open communication between the security and development teams. By sharing their unique challenges and responsibilities, both teams can develop a shared perspective, fostering empathy and understanding across the board. Empower the early-adopter cross-functional product teams identified in the prepare stage to identify common security gaps, initiatives to close that gap, and a couple of quick wins that the team is willing to commit to over the next three months. One such initiative might be the selection of DevSecOps tools using developer experience and automated remediation as important criteria, such as the criteria that I used in The Forrester Wave™: Software Composition Analysis Software, Q4 2024. Evaluation of tools must be done with input from both development and DevOps teams to ensure that they meet the needs of all stakeholders. In this phase, establish baseline metrics, such as the mean time to remediate security findings, to provide a tangible measure of progress and success.
- Walk and scale success. Adoption of DevSecOps practices now scales across the organization, propelled by the successes of early-adopter teams who share their achievements through internal roadshows. Product teams have automated security validation such as static application security testing (SAST), software composition analysis (SCA), and security scanning embedded into their pipelines and can expand coverage to testing APIs, infrastructure as code, and container images. But this automated scanning by multiple tools will generate an overwhelming number of security findings, with each categorizing the severity of issues in their own way. Normalize these findings, taking into account exploitability and other additional intelligence to prioritize them effectively. Watch developer velocity in this phase carefully, as you should realize faster development cycles. The integration of automated feedback loops within the development pipeline eliminates the need for developers to switch contexts between development and security tools, streamlining development.
- Run and achieve continuous security. As DevSecOps practices are expanded across various product teams to establish a culture of continuous security, it becomes essential to adapt and scale security knowledge accordingly. A key strategy involves implementing a developer security champion program. This gives security professionals more time to adopt a risk-based prioritization approach by pulling in signals and context from runtime and production, such as: Is the application internet-facing? Is it storing or transmitting personally identifiable information, payment card industry information, or protected health information? What is the priority to the business? What vulnerabilities can be leveraged for an attacker to move laterally? Security also has the time to crystallize “paved roads” — standardizing security templates and policies for continuous integration and continuous delivery pipelines, codifying security best practices, and providing product teams with secure and healthy libraries to use for authentication and authorization, encryption, and logging. Monitor metrics, such as the time to detect a security issue, patch it, and restore service in production. There is a temptation to reduce investment in further security initiatives and resources at this stage, but teams that choose to pause DevSecOps advancement or scale back on security professionals will be ill-equipped to tackle emerging security challenges introduced by new technologies, architectural shifts, and evolving software development methodologies. For example, embedded AI in customer-facing and internal applications and coding TuringBots will bring innovation but also require ongoing security investment to ensure that teams remain prepared and resilient against new threats.
Learn how to kick-start and manage your organization’s DevSecOps journey by attending my session, Secure Software At Speed With DevSecOps, on Tuesday, December 10, at the 2024 Forrester Security & Risk Summit!
Additionally, Forrester clients can see the complete DevSecOps model and best practices by reading DevSecOps Best Practices: Prepare, DevSecOps Best Practices: Crawl, DevSecOps Best Practices: Walk, and DevSecOps Best Practices: Run or by setting up an inquiry or guidance session with either myself or my coauthor, Christopher Condo.
(written with Danielle Chittem, research associate)
